In this article:
Applicable to:
- Twingate Component: Client | Resources
- Third Party Applications: Google Chrome, Microsoft Edge, Mozilla Firefox
Overview
DNS-over-HTTPS (DoH) is increasingly being enabled by default within web browsers to encrypt all DNS lookups. Twingate relies on a DNS proxy in order to intercept user traffic for private DNS Resources. Because DoH encrypts all DNS requests, this will result in private DNS resources protected by Twingate from being accessible to users. In order to prevent browsers bypassing the Twingate Client, we recommend disabling this feature.
Process
Note: If your organization uses an MDM solution for device management, it is very likely that these settings can be defined centrally and pushed out to all users.
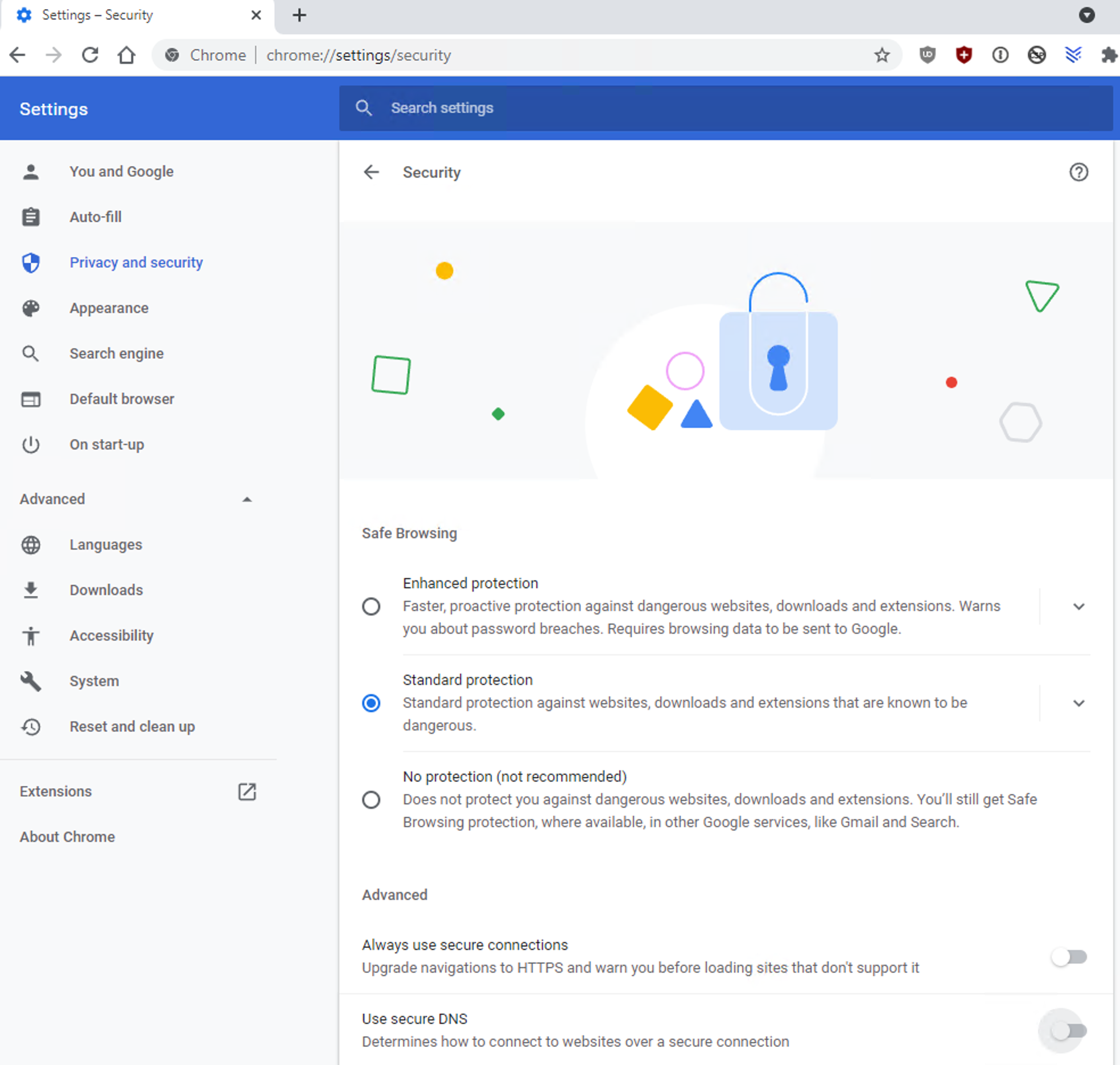
Google Chrome
DoH is enabled by default on Google Chrome version 83 and later. It can be disabled as follows:
- In Chrome, click the menu button and then click Settings.
- Go to Privacy and security and then Security.
- Scroll to Use Secure DNS and uncheck the option.
- Restart the browser.
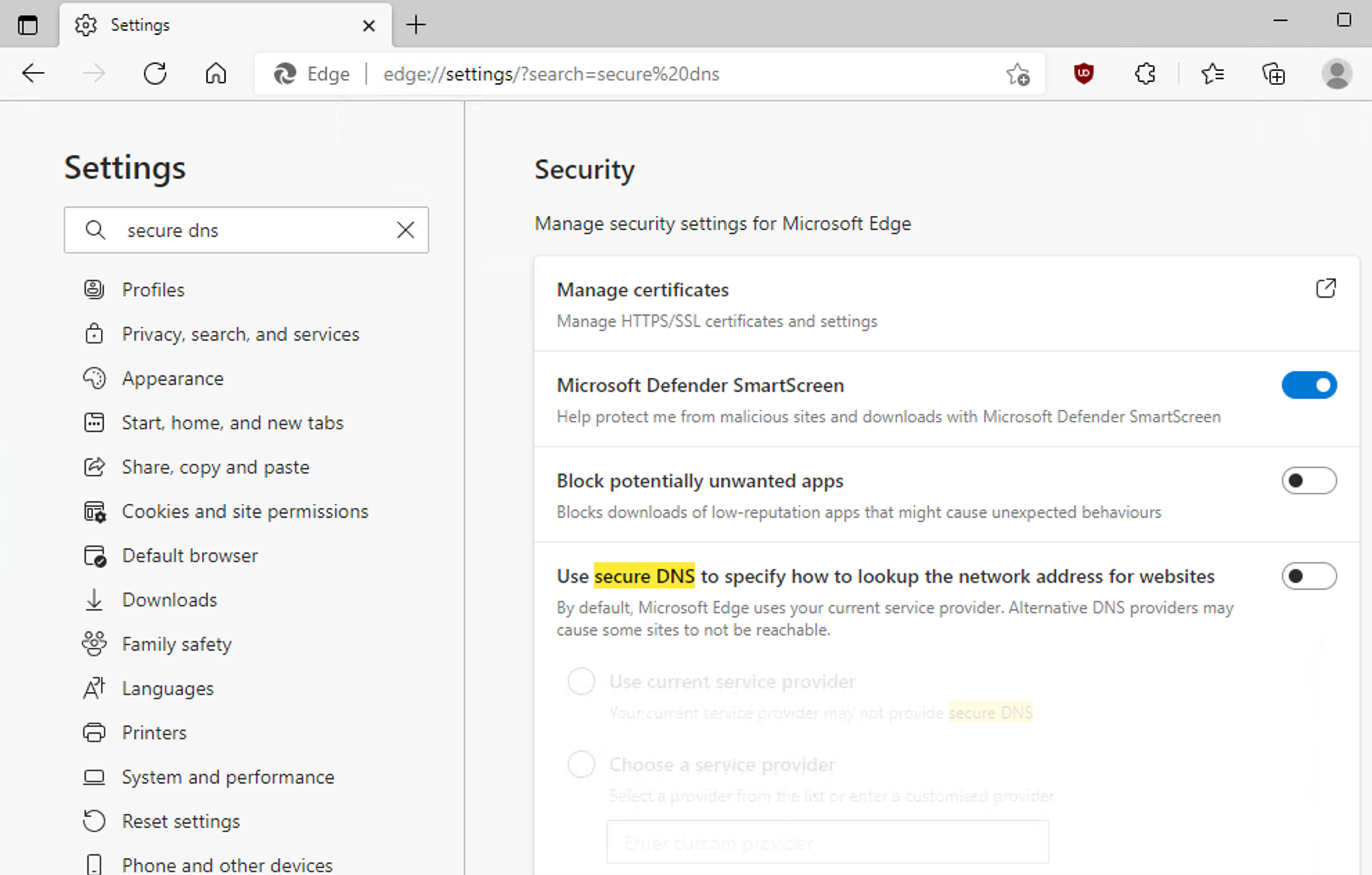
Microsoft Edge
Microsoft Edge, it can be disabled as follows:
- Click the menu button and then click Settings.
- In the search box type 'Secure DNS'.
- Scroll to Use secure DNS to specify how to lookup the network address for websites and uncheck the option.
- Restart the browser.
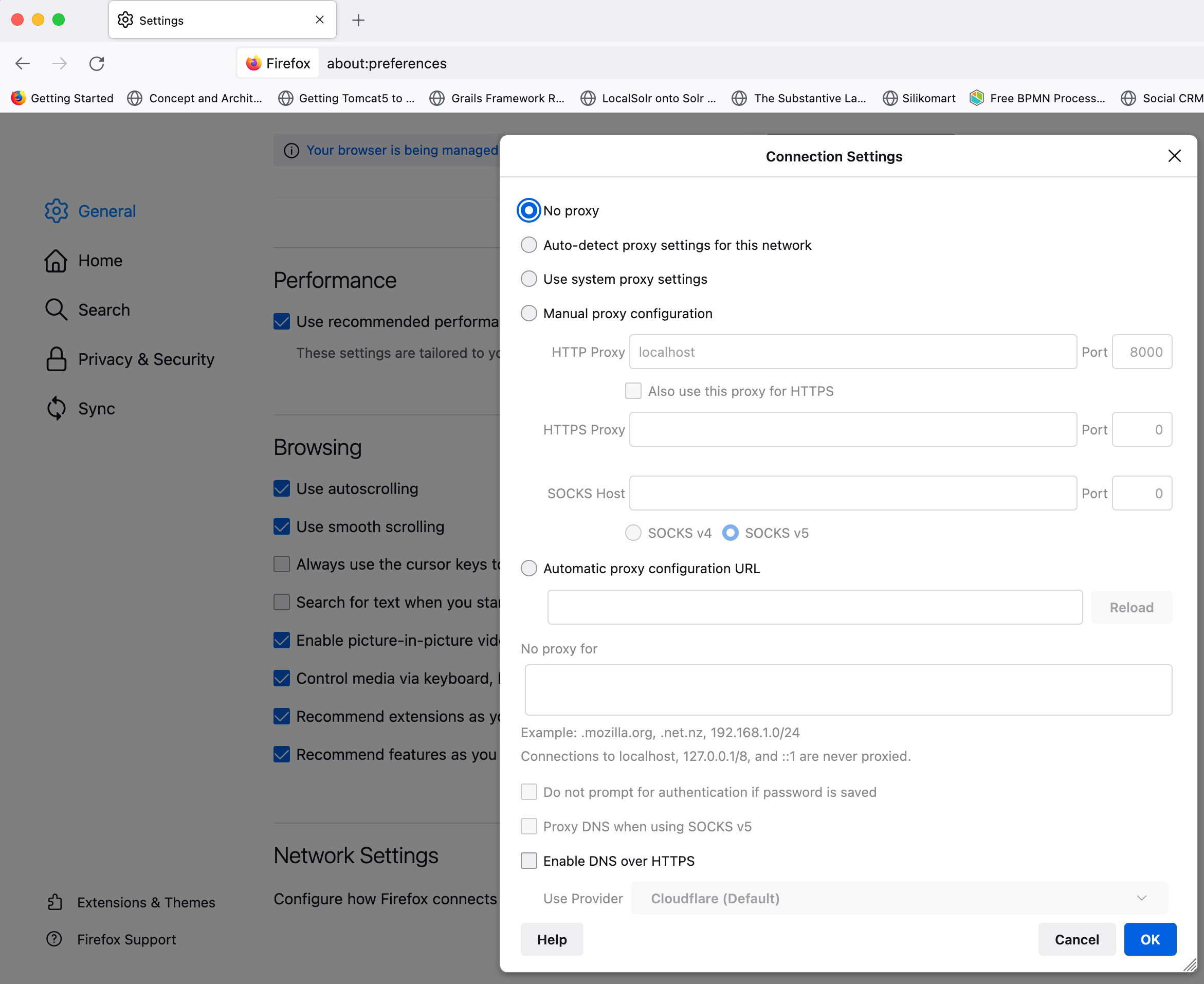
Mozilla Firefox
DoH is enabled by default on Firefox. It can be disabled as follows:
- In Mozilla Firefox, click the menu button and then click Settings.
- In the upper right search bar , search for Secure DNS
- Under Enable secure DNS using: select Off.
Prior to version 116
- In Mozilla Firefox, click the menu button and then click Settings.
- Scroll to the Network Settings section and click the Settings button.
- Scroll down to the Enable DNS over HTTPS option and uncheck the box.
- Click OK to save your settings.